“And then secondly, sir, does the Russian government have any compromising material on President Trump or his family?
PRESIDENT PUTIN: (As interpreted.) (Laughs.)”

Cyber-warfare specialists serving with the 175th Cyberspace Operations Group of the Maryland Air National Guard (U.S. Air Force photo by J.M. Eddins Jr.
Sometimes What You Think Happened Is What Someone Wants You To Think Happened.
By Robert Young Pelton
Note: The name of the cyber company and the owners have been changed.
It’s midnight in Manhattan, Friday January 13th, 2017 and someone is hacking into Rudolph Giuliani’s server at his corporate headquarters. A few hours earlier Giuliani, head of a cyber security provider and senior advisor to a law firm was just announced as Trump’s guru on cyber security for the President Elect. The timing of the hack less than a few hours later is not a coincidence. Giuliani’s cyber team had knocked off for the weekend at noon. Giuliani no stranger to the media but not known for his cyber security skills had appeared on Fox and Friends the day before to boast about his new cyber security effort.
I am on a conference call with the members of SybrTek (the name has been changed at the companies request), a new Texas-based cyber security and big data startup that could be described as the real world equivalent of the Cyber Expendables. Five men each with deep experience singularly and collectively inside the CIA, NSA, JSOC, NASA, SEALS and other government agencies. The “black” teams that support Special Mission Units and covert operations that go as far back as Angola and 80’s Afghanistan. Like a comic book super team, each has an unusual skill in addition to their military and intel training; hacking, jamming, disinformation, Psyops, etc, all honed in real world counter terrorism missions and now available for hire.
These men are not bespectacled nerds yelling “I’m in!” but they are combat vets pushing 60 with the usual assortment of paunches, bad necks, fading vision, military pension checks and about 150 combined years of experience fighting terrorists on the electronic and mud battlefields. They also know that demand for their services is high. America is losing the cyber war not because of terrorists or hackers, but because one of their main enemies was, and is, the glacial pace of their own government to adapt and change to new technology.
Now that they retired they are free to surf the big wave, 30 to 60-day cycle of cyber tool development. Not surprisingly their first clients were overseas. Sentiment tracking of the population for Saudi Arabia’s government to measure the impact of change was one task. Could the kingdom survive a sales tax? How far could they shift to more moderate politics without triggering an uprising? These dull questions are the lifeblood of data analytics.
Their new company deals with the never ending and ever changing problems of hackers; The high level and low level espionage that has been hogging the headlines every since Hillary Clinton wiped her server with a cloth. These men battle in the world of Information Operations aka Strategic Communications aka psyops aka Influence Operations aka dirty tricks. A battleground of selective and targeted information designed to create an alternative universe.
This might require deceiving your opponent, hacking the enemy, black bagging a server by breaking in and physically stealing computers and hard drivers, creating rumors or fake news or even generating false documents (the OSS called them “Black Letters” in World II), use psychographic profiles to target and rile up certain “excitable”groups, create confusion by rapidly injecting conflicting evidence or statements, run “false flag” operations to fool the enemy and even distribute manufactured or real scandal that might include video of sexual activity, something the Russians call “kompromat”.
Most of these tactics are not actually the end result but are created by proxies to generate secondary and tertiary effects like public outrage, scandal, loss of confidence. Ideally a population can be controlled by outside forces if they lose trust in their leaders, leaders are less subject to accountability if the media loses the trust of the public in publishing what is true and what is false.
This group of battered and bruised warriors, hope their dark mastery of the full spectrum of “strategic communications” will match the government, business and public’s sudden realization that the once militarized doctrine of psyops has now become a everyday marketing weapon against civilians. The recent publicity involving Cambridge Analytica, Facebook and election marketing are just a few examples of a new deceptive assault on our senses and thought process.
They hope that harnessing their skills of gathering human intelligence to understanding marketing trends, to even geo-targeting individuals to within a 3 by 3-foot space will provide truth and clarity to clients. Tonight however, they are just trying to find someone to report the hack of Giuliani to. Something the SybrTek team had been doing for members of the Trump transition team since the summer of 2016.
+ + +
Finally our interview was interrupted by an urgent telephone call from the client. “Someone is trying to hacking Giuliani” repeats the former operative to the computer executive as he watches the screen on his laptop. The hacker has logged in through a backdoor on Giuliani’s site put there by Anonymous. “Somebody didn’t put a patch on some old software and they are in” says one cyber analyst. “You can tell Anonymous by its malware” he says matter of factly while watching the digital stranger poke around Giuliani’s New York-based server called http://giulianipartners.com.. The timing is perfect. Maybe the new government will take cyber security seriously and they might get a contract.
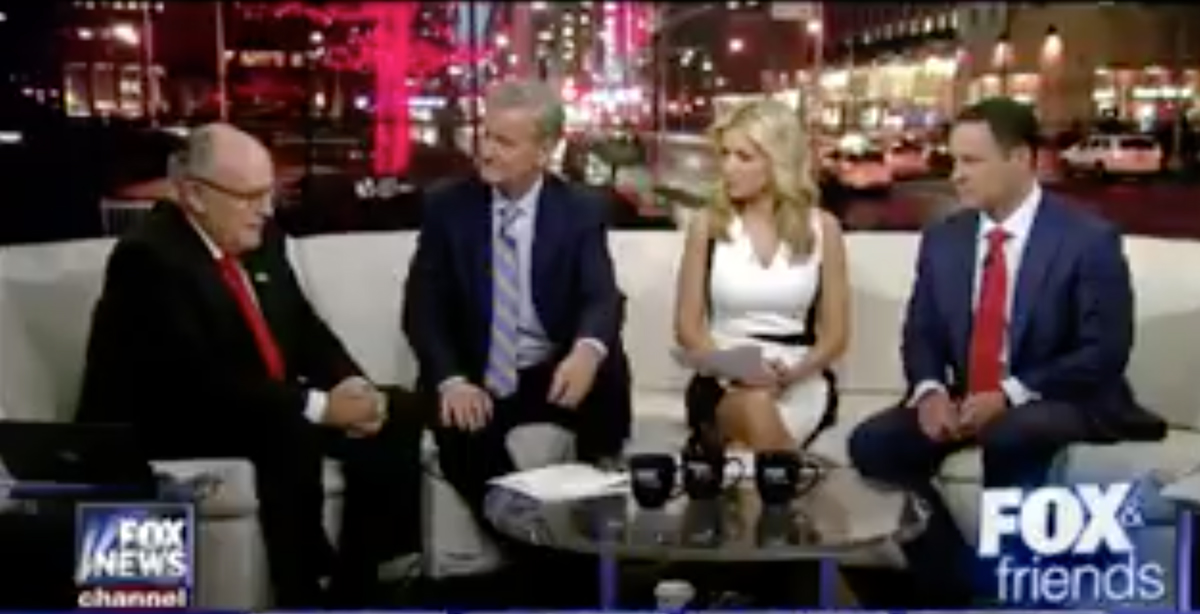
January 12, 2016 – Rudy Giuliani on Fox and Friends discussing his new role as cyber security organizer for President Trump. His server was hacked hours later.
In early January of 2016, Presidential candidate Donald Trump mentioned that he would bring in private individuals to work on cyber security. He was quickly learning that the vast machine that is the government is slow to react and even slower to adopt rapidly changing threats against computer systems. That 30 – 90 day battlefield during which hackers and counter hackers joust back and forth, generating new software and tricks.
Rudolph Giuliani then went on Fox & Friends on the morning of January 12, saying that he was going to “coordinate all this“. Giuliani is not known for having any experience in cyber security but he did have a consultancy and had a broad business based from his post 9/11 popularity. By that evening, his server was under assault. Keep in mind, it wasn’t the hack, there was nothing of value on the cheap web page, it was the secondary effect of being hacked, that the hackers were after.
Russians weren’t doing the hacking. That night on Twitter, Kansas-based cyber security expert, Michael Fienen found himself the star of a real time social media crowd attack on Giuliani’s server as thousands of computer nerds began picking apart every aspect of the Giuliani’s servers security or lack thereof. After a long night of real time tweets and surprised at his sudden viral fame, he posted. “If I’d known this was gonna blow up like it did, I’d have given it a witty hashtag. Someone else said #RudyOnRails (a pun on Ruby On Rails open source software) and that made me laugh.”
Tech critics publicly lambasted Giuliani’s system and his simple page for being outdated and easy to penetrate. Critics pointed that the web site using doing everything wrong from running Flash to having multiple open ports to having an expired SSL certificate. It wasn’t that hard.
+ + +
“Hacking”, the criminal electronic act of breaking and entering into a computer or email system to steal or access information is little different than the 1972 Watergate break in and wiretapping of the Democratic National Headquarters hatched by ex-FBI agent, G. Gordon Libby. That analog hack was discovered by a night watchman and later exposed to be part of a much more nefarious election plan by journalists Bob Woodward and Carl Bernstein of the Washington Post. Although hacking is a common as physical theft, the act becomes magnified during political campaigns generating doubt in “the system”. A fictional idea that governments are somehow secure and moral. Political hacking adds a cinematic measure of deceit and intrigue when compared to simply data or information theft from consumers.
In the room with the SybrTekpatched in by phone, the conversation stops as they monitor the activity going in and out of the giulianipartners.com server.
“Holy shit, they just sent Giuliani an email from his own server.
“Did you contact him?
“I just sent one of his guy’s a text”
“Do you want to stop it? This is going to be really fucking embarrassing tomorrow if he gets in”
“We can’t, it’s against the law, we could but a bot on this and send it back to the hacker”
This hack on Giuliani is just one of thousands of attempts every minute against high profile targets particularly against members of political parties. And they are almost impossible to stop and harder to prosecute. Again, this real life hacking scenario was designed to have what is called a “secondary effect”: Embarrassing a Trump team member with the idea that a cyber consultant got hacked within hours of the announcement. Much like the search for Clinton’s missing or deleted or classified emails became the singular scandal of the election.
This hack occurs just after midnight, there is no one in the office, it is when most companies back up their files and if the hacker findsanything of value the appointment of Giuliani and the media payments for scandalous dumps would make the exercise worthwhile. Luckily it is caught and reported to the government authorities by SybrTek. Again, hacking favors the criminal because counter hacking is just as illegal as hacking.
+ + +
The SybrTekcrew rattle off a list of major hacks of political figures on both election teams in the last few months. Jim (an alias) for a former Navy SEAL says “Information is worth money. There is a $30,000 bounty from Wikileaks for anyone providing proof that Obama is deleting or dumping data. Hackers have been after Trump, his family, the foundations and major supporters forever.”
Jim insists that in the closing hours of the Obama administration IT techs were removing the markers from hard drivers rendering them impossible to search but maintaining the data on the drives.
“Trump can brag that the RNC didn’t get hacked but it was actually just easier to hack the DNC.”
Hacking is illegal, it’s theft, digital breaking and entry, but it is the new normal. Millions and millions of servers have been compromised with all the sensitive and exploitable data along with. Swingers sites like Ashley Madison, email accounts like Yahoo, financial sites complete with addresses, credit card numbers and even the Federal Government’s employee data all end up somewhere for sale somewhere. It’s not personal, it is just a business.
Listening to the real time hack and discussion in the background, we discuss just how vulnerable our government and their employees are.
“The transition team’s emails are all compromised” says Ray, a former CIA Special Activities Division/Ground Branch officer and Marine, “we were helping some of the team defend against hackers on their personal and business emails but they now have to use a dot gov address. We discovered that the transition emails were hacked in 2008 and 2009 with malware that the government didn’t’ notice. Why because they didn’t’ need to use them in 2012 and it wasn’t until a few weeks ago that we ran some tests and found the bug. We reported it to the NCCIC National Cyber Security and Communications Integration Center and a few other places. That bug has gone on to infect 140 different government departments.” Ray explains. “We could fix it quickly but then again it would be against the law” Ray says with a slice of irony. According to the 586-page report records and submissions to the NCCIC, as of January 13,2017 so far nothing has been done by the Department of Homeland Security.
+ + +
“I will say this: I don’t see any reason why it would be, but I really do want to see the server. But I have — I have confidence in both parties. I really believe that this will probably go on for a while, but I don’t think it can go on without finding out what happened to the server. What happened to the servers of the Pakistani gentleman that worked on the DNC? Where are those servers? They’re missing. Where are they? What happened to Hillary Clinton’s emails? Thirty-three thousand emails gone — just gone. I think, in Russia, they wouldn’t be gone so easily. I think it’s a disgrace that we can’t get Hillary Clinton’s 33,000 emails” – President Donald Trump
The Intelligence community insists that America is at war with hackers, specifically Russian hackers. On January 2017, the DNI released a comprehensive report, “Background to “Assessing Russian Activities and Intentions, in Recent US Elections”: The Analytic Process and Cyber Incident Attribution”. On Friday July 13, 2018 the DoJ indicted 12 Russian hackers and alleged that Russian intelligence agents were behind the hack of the Democratic National Committee and other computers. The indictment is very focused, much of this publicity on hacking, cyber security and missing emails started with the controversy around Hillary Clinton’s use of private servers and the deletion of an estimated 31,830 of the 62,320 emails on her server.
The indictment was also well timed, being dropped just before President Trump was to meet with Russian President Vladimir Putin. It was clear, the Department of Justice and related agencies were painting a red bullseye on Vladimir Putin, a former Russian spy and naming names. Just before President Donald Trump was about to make a “grand bargain“, in a private meeting and with Russia, America’s former public enemy #1
But let’s go back
The connection between President Trump and SybrTek began with Lt General Mike Flynn. Some of the men on the team worked with Flynn’s during his 33-year military career, particularly during his time in Iraq and Afghanistan. Flynn is now a civilian and in the early days of the campaign, was often seen at the side of the yellow haired, casino owner turned reality TV host. The flamboyant Trump and his grim-faced war horse advisor made for an odd couple A lifetime Democrat, Flynn was part of an advisory group of ex-intel leaders who made themselves available to council candidates about the threats to national security. In July of 2016 Flynn had released a book penned by well-known Neocon Michael Ledeen called “The Field of Fight: How We Can Win the Global War Against Radical Islam and Its Allies Hardcover” and was quite vocal about the need to destroy ISIS. The hatchet faced and taciturn Flynn had a calming effect on Trump during the campaign according to the SybrTekteam members.
Flynn became a sage advisor who provided Trump clear analysis of confusing events, his battle cred and rough style also appealed to Trump’s fans. Not surprisingly, Flynn was Trump’s original pick for Vice President. A few off-putting TV appearances and some over enthusiastic public speeches in which he led anti-Hillary chants to “Lock Her Up” showed that the man who worked in the shadows might not be cut out to be in the glare of the spotlight. Flynn also had enemies on home turf. In addition to his hardline view on ISIS, Flynn’s greatest sin is that he wanted to stop the revolving door black budget gravy train inside the major intelligence agencies. Money that is generously back doored to faithful intel retirees. Money that is in the billions and will never be held accountable to the public. Back i January of 2010. Flynn even suggested that spies should be more like journalists in a controversial report that surprised the intelligence community.

The military has some of the most sophisticated computer tools and techniques. The problem is we fight wars in counties where even electricity is an innovation.
Although Flynn was an Obama pick to run the DIA, Flynn’s aggressive style soon banded the career bureaucrats together into an angry cabal and he was forced out a year early. In demand as an intel pundit, he started Flynn Intel Group. His equally aggressive efforts to woo foreign clients became the target of negative media, focusing on his unregistered lobbying and foreign meetings to pitch his intel firm including his dinner in Russia for Russia Today. At the dinner afterwards Vladimir Putin walked about and sat next to Flynn. Suddenly he was viewed as a Russian proxy. Nobody really held up his client list to see that it also included a wide variety of Middle Eastern and other countries that we do deals with.
Flynn’s new media fame also led to an intensification of hacks on his platforms. In early July 2016, SybrTek told Flynn that his phone had been compromised. Nothing sensitive “I’m an open book” he told the SybrTek team but still, someone was targeting the Trump campaign team.
SybrTekquickly found the sender of the phishing email that led to the hack. The ISP, caller code, originators address, registered database was open source. Which led them to two different servers in Poland.
The team then traced the hacker back to yet another server located a small town of 100,000 people in the Carpathian Mountains in Romania. They hard pinged a location in a town called Râmnicu Vâlcea.
They quickly found a person attached to the server. A young female Romanian hacker. Ray remembers seeing her profile picture, “She was cute. She did her homework. She was offering her services at 700 euro to target and hack anyone you wanted. It’s a business. Turned out she had emptied Flynn’s phone… and we found other things.”
Three weeks before the July 18th Republican convention, the SybrTek team not only found Flynn’s stolen data but stolen data (not emails) from journalist and Clinton confidante and former journalist Sidney Blumenthal That wasn’t all there was embarrassing material on Hillary Clinton and Donald Trump kept on that same server. They won’t discuss what they found. “Embarrassing” is all they will say about the files. What they found were Clinton’s medical records stolen from a visit to a doctor in Germany.
The team then reported to the government that they had found sensitive information sitting on a foreign server on both parties. These files on either former candidates have not been released to the media or public. The hackers who hack the hackers are paid to keep their mouth shut and they don’t want to get caught up in the polarized media hysteria that doesn’t understand the world of hacking.
They are quite vocal about the stunning lapses in simple security taken by both Clinton (who was discovered to be using a private unsecured home computer for government business) and the DNC, an organization that had security systems penciled in for installation but never actually installed them.
Although internal government agencies were concerned about Clinton’s use of a private emails system as early as 2009, hackers had tried numerous times to breach Clinton’s basement stored Apple server. in Chappaqua, New York. It wasn’t until a December 2012, FOIA request from Citizens for Responsibility and Ethics in Washington came up empty that the public began to wonder where Clinton’s emails actually were. In June of 2013, Clinton hired Platte River Servers who physically moved her home-based server into a data service center in New Jersey.
+++
Clinton finally hired an expert to deal with data after Romanian hacker named “Guccifer” dumped a number of emails between Clinton and insider Sidney Blumenthal in March of 2013, Clinton’s private server came to light. Throughout the Benghazi investigation, the idea of Clinton not ever using a .gov email address never really took hold. Her motivation appeared simple. She and her staff wanted to keep their communications simple away from FOIAs and government employees. Her excuse was that any emails she sent would be resident on the recipient’s government servers. There were concerns about her servers handling sensitive and classified information. These questions would lead to a July, 2016 FBI investigation.
New York Times broke the story in March 2, 2015 letting the world know that Clinton had been using a personal computer at home since 2009. Based on Guccifer’s boasting and Clinton’s high profile address but low profile security, by then the DNC and Clinton staffers and most likely Clinton’s computer had been under attack and most likely had been compromised. The data, movements, communications, plans and files of the former President of the United States, his family and the current Secretary of State would be of the highest interest to all foreign intelligence agencies. Various tech experts and government officials pointed out that Clinton initially operated her laptop and Blackberry without encryption software making it extraordinarily easy to hack her and other people who communicated with her. In Part Two we will explore just how badly compromised the White House was.
It would be relevant to note that there was little to no mention of Russia in any of this initial U.S. media and political generated furor over Clinton’s lax security and mishandling of government files. There is also the given that hackers have little incentive to broadcast their break in’s. They are happy to sift and sort through compromised computers for years if needed. Had Clinton been hacked? Well her friends had. Why not her email.
+++
On January, 22, 2014, a 40-year old Romanian named Marcel Lazar Lehel was arrestedin Arad near his village of Sâmbăteni. Arad 337 miles west of Bucharest. Lehel was “Guccifer”. In 2013, Guccifer had hacked in a computer and found jpg’s with President George Bush’s home paintings including one of the naked Bush in his bathtub. He stole them from the former president’s sister and he guessed her personal security codes by using Wikipedia.
He had also been busy hacking “into the email and social media accounts of high-profile victims, including a family member of two former U.S. presidents, a former U.S. Cabinet member, a former member of the U.S. Joint Chiefs of Staff and a former presidential advisor” according to the nine count DoJ indictment. It was determined that Guccifer was busy hacking between December 2012 to January 2014 mostly out of boredom since he was not working his normal job as taxi driver.
Blumenthal’s files found on the Romanian server, according to the FBI were dated from January 2012. As Hillary Clinton quite rightly predicted, her emails were on other people’s servers just not government ones. Regardless of what security protection Clinton had or didn’t have, her emails were clearly being hacked through her associate’s computers.
In May of 2016, Guccifer told Fox News reporter Catherine Herridge that he had breached Clinton’s server in early 2013 and it was “easy” not just for Lazar but for “everybody”. In the jailhouse interview Lazar provided detailed information on how he breached the server. Lazar also hacked Clinton confidante, Sydney Blumenthal’s AOL emails in March of 2013. The Romanian insisted that all he had to do was find Clinton’s IP, wait until the ports were open and use software to breach the data. He told Fox “As far as I remember, yes, there were … up to 10, like, IPs from other parts of the world,” referring to other hackers online at the same time. Guccifer’s favorite hack was to reset the password and then use Wikipedia and Google to find the names of pets, or schools used as security questions.
There is no evidence that Clinton’s servers were compromised by Lazar other than Guccifer’s statements, but Clinton’s servers were compromised as we will find out in Part Two. Things started getting serious in the Spring of 2016…two years after Guccifer went to jail.
+++
A Wikileaks document dated March 19, 2016 details how John Podesta, Chairman of Hillary Clinton’s campaign received an email from Gmail notifying that someone had logged into his personal Gmail account and to please click on the email to enter his username and password so it could be changed. Podesta’s Chief of Staff, Sara Latham then pinged the campaign staff tech consultant Charles Delavan (both of whom were was using a hillaryclinton.com email, not the Gmail account in questions). Delvan responded:
“Sara, This is a legitimate email. John needs to change his password immediately and ensure that two-factor authentication is turned on his account. He can go to this link: https://myaccount.google.com/security to do both. It is absolutely imperative that this is done ASAP.”
The source of log in was identified by Google as:
Saturday, 19 March 8:34:30 UTC
IP Address: 134.249.139.239
Location: Ukraine
Podesta or his assistant then inexplicably used the phishing link in the email rather than the link Delavan provided. This simple act opened a back door to all of Podesta’s emails and any passwords he may have typed into those emails and more importantly the ability to fool other people on his email list into opening what looked like legitimate documents from Podesta. Again a hacker only reveals their presence once they feel they have enough data to sell. If a freelancer was to market real time access to the DNCs strategy and communications during an election, it would hard to put a price on that access.
Delavan later insisted he meant to type “illegitimate” rather than the word “legitimate” to describe the phishing email.
This is where it starts to get weird. DNC leaders were tipped to the hack in late April 2016 after some had gained entry to the DCCC and then used stolen credentials to then gain entry into the DNC system. The DNC insists that the breach was discovered the month before in April. Not coincidently a site called “DC Leaks” was registered on April 19, 2016. This hack by what was now a team calling themselves Guccifer 2.0 was professional and aggressive. Unlike the more random Guccifer 1.0 , this 2.0 Guccifer appeared to be politically motivated. The goal appeared to get as many files into the public domain even though few of them qualified as “Clinton Dirt” Over 300 individuals related to Clinton’s campaign and the Democratic political groups had been targeted since March but no Clinton dirt.
There was dirt on Trump. Not very dirty dirt, but it generated the perception that there was an embarrasing dossier on Trump .
Among the files leaked on June 15, was a massive “oppo” file on Donald Trump. Not the more famous and rancid “golden shower” dossier published in January 2017 by Buzzfeed. The first oppo file was a massive unreadable collection of open source articles. It was the Steele dossier, which was not hacked, that began to push the Russian/Trump narrative. The Steele file was not only a work in progress but had been actively shopped around to major media outlets who found the accusations salacious and potentially libelous. The shopping began in October 2016, with Mother Jones and that was after Steele had handed over the report in July 2016 to the FBI. The FBI initially agreed to continue to fund Steele’s work but changed their mind. The main architects were a research company called Fusion GPS who inexplicably had clients Natalia Veselnitskaya and Rinat Akhmetshin. According to the New York Times, Glen Simpson was not only developing dirt on Clinton via Steele, but working for a law firm, BakerHostetler, representing Prevezon Holdings, the company who had also hired Veselnitskaya and Akhmetshin to dig up dirt and attack Bill Browder, the man behind the Magnitsky Act.
“He’s a professional smear campaigner and liar for money,” Browder lashed out at Simpson in the New York Times. “The credibility of anything that he does is in question.”
The Steele Dossier as it became known, is classic Russian kompromat and clearly attempts to link Trump to Russia influence via blackmail and financial dealings with dirty bits sprinkled in to catch the media’s attention. James Comey of the FBI notified President Trump on January 6, 2017 that the intelligence community believed the Russians were attempting to interfere with the election. On January 10, Buzzfeed published the Steele dossier. The singular document had shifted the focus from Hillary Clinton’s use of a private server to the potential of a Russian asset running the country. A perfect secondary effect of psyops.
Remember this is not the massive 211 page open source opposition report that focuses mostly on Trump’s marriages and business squables using published articles. This clear attempt to conflate one “leaked” dossier with one that created and shopped after the election began the slow spin of the media towards linking Russia with Trump. An accusation that continues to gather speed and substance as Special Prosecutor Robert Mueller continues his investigation and the FBI indicts Russians and Trump associates in numerous indictments. But the reality was that Trump didn’t win the popular vote, Hillary Clinton did. And the victory in the election was decided by the electoral college.
Where did the idea that Russia had hacked the election and linked to Donald Trump come from?